Calmer
bug bounty programs
for startups
Security researchers from all over the world will help you find and remediate high-risk vulnerabilities before attackers do.
Trusted by some of the world’s most innovative companies
Continuous testing;
Only signal, no noise
Your engineers care about security, but you know you don’t have the resources internally to test
your application and infrastructure as thoroughly as you’d like.
A bug bounty program is one of the most effective ways to secure your software. They incentivize
a wide range of researchers with varied skills to continuously and independently test for
vulnerabilities.

Federacy has been a great security partner. Their team is incredibly thorough in their testing and their deep knowledge around all things security and engineering has been invaluable for our fast-moving team. We've really enjoyed the level of support they provide via Slack as well.
Sumukh Sridhara General Manager, AngelList Venture
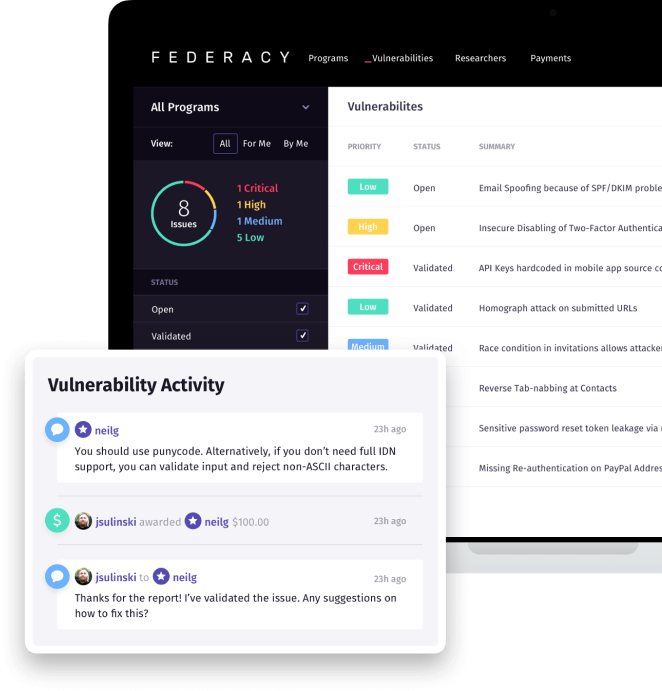
Powerful vulnerability management
While we actively test for three weeks, we engage for the entire year, almost like a lightweight outsourced-CISO, available via Slack to answer any and all-security related questions. We’re available to help with architectural and security tooling decisions, dependency risk assessment, vulnerability remediation, and many other areas.
The best security researchers in the world
Federacy security researchers have studied or worked at such institutions as MIT, Carnegie Mellon, CERT, Google, Twitter, and PricewaterhouseCoopers. They are OSCP, OSCE, CISSP, CREST, and CEH certified. We work in teams and focus on vulnerability chaining, business logic, authentication and authorization.
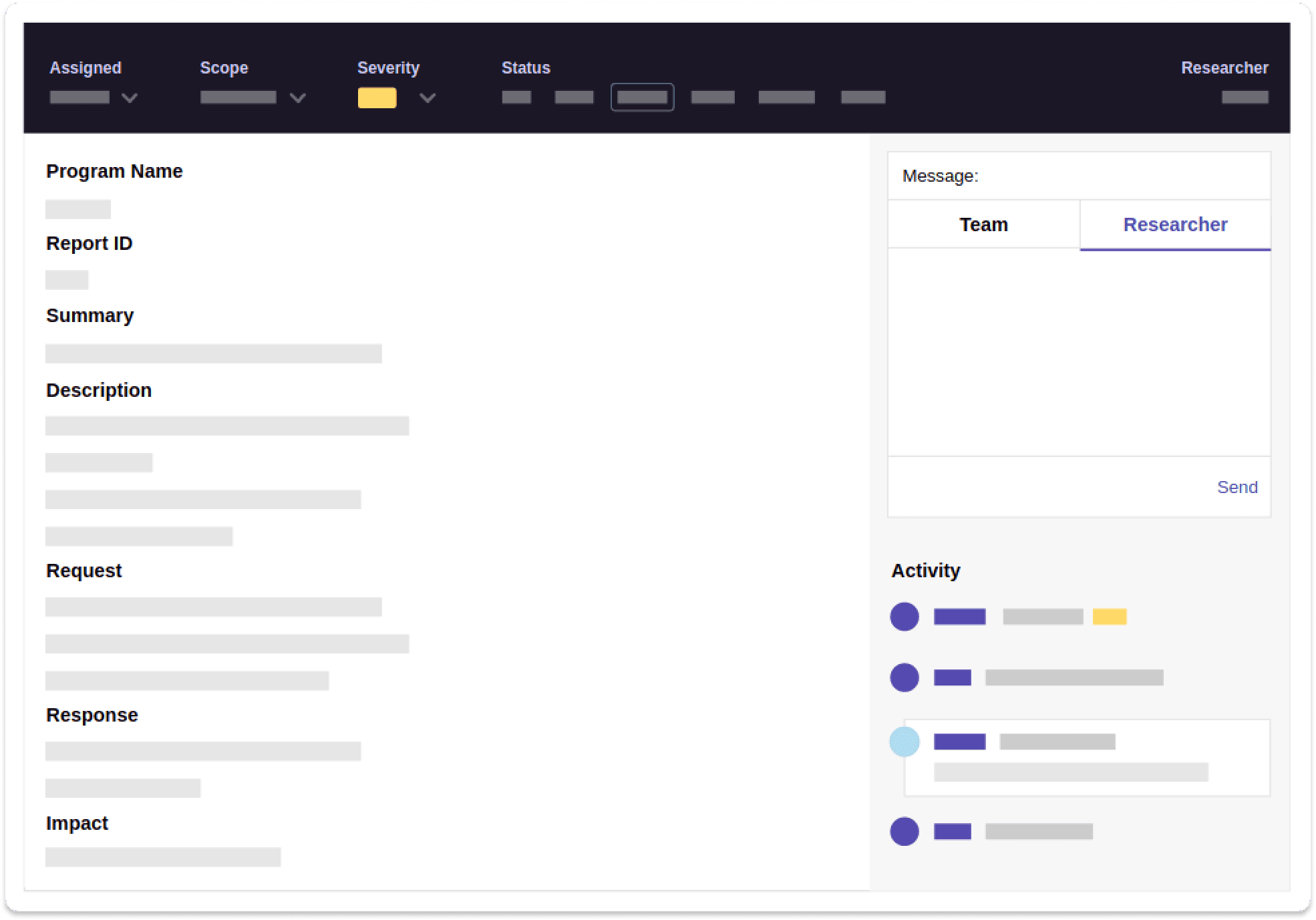

Triage, remediation assistance, and on-demand, CISO-like guidance included
For our managed programs, we augment your team by staffing a shared Slack channel and are available to support you beyond just triaging your bug bounty reports. This enables us to help with remediation in real-time and provides a place to discuss higher-level security or architectural topics.
Deep research
We take the time to document and learn the ins-and-outs of your applications and APIs for several
reasons: to answer questions from researchers, understand your mitigative controls, and thoroughly
evaluate the impact of a vulnerability, particularly looking for chaining potential with other
known issues.
Our researchers primarily focus on legitimately impactful vulnerabilities, such as IDOR, RCE, and
SSRF, which could lead to breach notification requirements if detected by someone with malicious
intent.
Simple pricing
Disclosure
-
Vulnerability inbox
-
Disclosure policy
Bug Bounty
-
All Disclosure Program features
-
Onboarding & VDP assistance
-
Report awarding
-
Private programs
Managed
-
All Bug Bounty features
-
Report triage and validation
-
Slack channel for remediation advice
-
Managed by Federacy badge
Pre-seed startup, non-profit, or open source project? Use Federacy for free
Let’s work together
We’d love to learn more about your company. Send us a message using the form below and one of our founders will get back to you quickly.
